Question:
How to troubleshoot SSH Single-Sign-On (SSO) and nested SSO?
Answer:
For general SSH SSO issues, please check the followings :
1. Before proceed to check the settings of the SSH nested SSO, please make sure that there are no DNS issues. This can be checked with the nslookup command. For example :
[root@xxxyyy machine]# nslookup xxxyyy.your_domain.com
Server: 192.168.3.61
Address: 192.168.3.61#53
Name: xxxyyy.your_domain.com
Address: 192.168.3.66
[root@xxxyyy machine]# nslookup 192.168.3.66
Server: 192.168.3.61
Address: 192.168.3.61#53
66.3.168.192.in-addr.arpa name =xxxyyy.your_domain.com.
Kerberos needs the reverse lookup record in order to request a correct service ticket
2. Please make sure that the FQDN e.g. xxxyyy.your_domain.com is used when ssh from Putty or Linux computer to another computer i.e. ssh xxxyyy.your_domain.com
3. Please check if it is running CentrifySSH or OpenSSH :
ps -ef | grep ssh
If it is Centrify's OpenSSH, it should look like this:
root 254202 155822 0 Apr 08 - 0:00 /usr/share/centrifydc/sbin/sshd
If it is stock SSH, it should look like this:
root 12427 1 0 Feb15 00:00:04 /usr/sbin/sshd
4. On the server side, please also check if the GSSAPI settings are enabled in sshd_config:
GSSAPIAuthentication yes
GSSAPIKeyExchange yes (If supported by Stock OpenSSH)
GSSAPICleanupCredentials yes
(If using ssh client instead of putty) On client side, please check the following parameters in ssh_config :
GSSAPIAuthentication yes
GSSAPIKeyExchange yes
GSSAPIDelegateCredentials yes
If any changes were made to the parameters, please restart the sshd process.
Restart the Centrify sshd:
#/etc/init.d/centrify-sshd restart
or
Restart the Open sshd :
#/etc/init.d/sshd restart
5. Please check the UPN e.g. test@domain.com (e.g. AD user test) is correct in the file .k5login under the /home/$user e.g. /home/test directory.
6. Please also check the group ownership and files permission of the AD user to make sure that there are no inconsistencies of the group ownership of the AD user and its corresponding files and directories of the .ssh directory, .k5login e.g. under /home/test6 as follows :
[root@rhel_w2 home]# ls -l /home
drwx------. 25 test6 test6 4096 May 16 04:34 test6
[root@rhel_w2 home]# ls -la ~/
drwx------. 25 test6 test6 4096 May 16 05:01 .ssh
[test6@rhel_w2 ~]$ ls -la ~/.k5login
-rw-------. 2 test6 test6 42 May 27 00:52 /home/test6/.k5login
[root@rhel_w2 test6]# cd ~/.ssh
[root@rhel_w2 .ssh]# ls -la
total 12
drwx------. 2 test6 test6 4096 May 13 05:36 .
drwx------. 25 test6 test6 4096 May 16 04:34 ..
-rw-r--r--. 1 test6 test6 419 May 13 05:36 known_hosts
[root@rhel_w2 .ssh]#
7. After checking the correctness of the configuration parameters in ssh_config and sshd_config, the next is comment out pam_fprintd.so in the /etc/pam.d/system-auth file if it exists on specific platform of OS (KB-2527).
For SSH nested SSO issue, please also check the following :
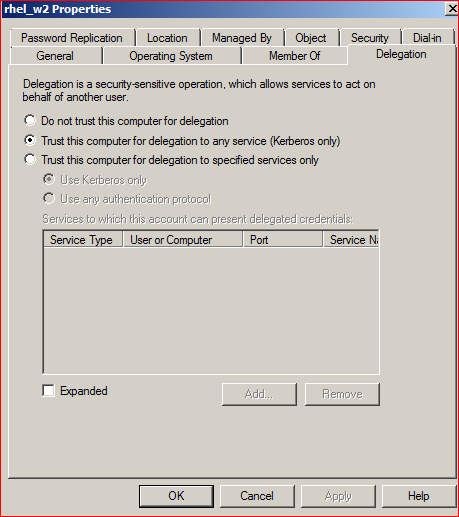
8. Verified the trust for delegation option of the computer/server by looking up ADUC of the DC :
If the location of the computer/server is not known, it can be found as follows :
ADUC>Action>Find> Find:Computer, Name: your_computer>Find Now > Double click on the computer>Delegation > Trust this computer for delegation to any service (Kerberos only) > apply/OK
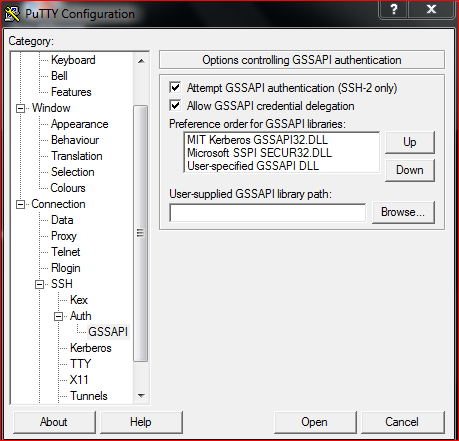
 9. If conneciton is issued from Putty, please make sure the following is checked:
9. If conneciton is issued from Putty, please make sure the following is checked:
Connection > SSH > Auth>GSSAPI > checked the Allow GSSAPI credential delegation
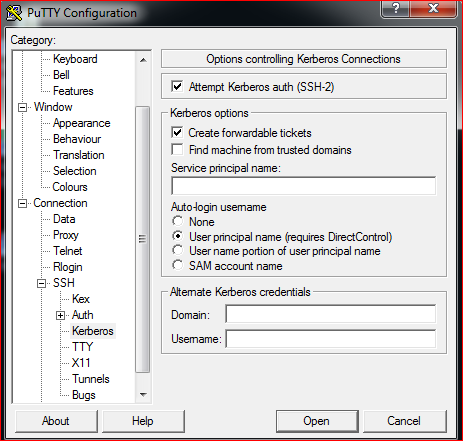
Connection > SSH > Kerberos > checked the Create forwardable tickets and enable “Attempt Kerberos auth (SSH-2)”
10. Tried nested SSO and go back to the first hop and run klist -f to confirm the host ticket has the "O" flag as follows :
In the client or server computer, login as AD user :
[test8@rhel_w1 ~]$ /usr/share/centrifydc/kerberos/bin/klist -f
Ticket cache: FILE:/tmp/krb5cc_cdc1593836722_pXddnv
Default principal: test8@CENTRIFY.LOCAL
Valid starting Expires Service principal
04/11/14 03:41:01 04/11/14 13:41:01 krbtgt/CENTRIFY.LOCAL@CENTRIFY.LOCAL
renew until 04/18/14 03:41:01, Flags: FRIA
Login to another host:
[test8@rhel_w1 ~]$ ssh rhel_w2.centrify.local
Red Hat Enterprise Linux Client release 6.4 (Santiago)
Kernel 2.6.32-358.el6.x86_64 on an x86_64
Last login: Thu Apr 10 08:47:31 2014 from win7c2.centrify.local
[test8@rhel_w2 ~]$ /usr/share/centrifydc/kerberos/bin/klist -f
Ticket cache: FILE:/tmp/krb5cc_cdc1593836722_C8OiTq
Default principal: test8@CENTRIFY.LOCAL
Valid starting Expires Service principal
04/11/14 03:41:01 04/11/14 13:41:01 krbtgt/CENTRIFY.LOCAL@CENTRIFY.LOCAL
renew until 04/18/14 03:41:01, Flags: FRIA
[test8@rhel_w2 ~]$ exit
logout
Connection to localhost closed.
[test8@rhel_w1 ~]$ /usr/share/centrifydc/kerberos/bin/klist -f
Ticket cache: FILE:/tmp/krb5cc_cdc1593836722_pXddnv
Default principal: test8@CENTRIFY.LOCAL
Valid starting Expires Service principal
04/11/14 03:41:01 04/11/14 13:41:01 krbtgt/CENTRIFY.LOCAL@CENTRIFY.LOCAL
renew until 04/18/14 03:41:01, Flags: FRIA
04/11/14 03:43:05 04/11/14 13:41:01 host/rhel_w2.centrify.local@CENTRIFY.LOCAL
renew until 04/18/14 03:41:01, Flags: FRAO
[test8@rhel_w1 ~]$
If the "O" flag is not set, please make sure "Trust for delegation" mentioned in step 7 has been configured. If this is not set, please either set it in "Active Directory User and Computers" or run adleave and adjoin with "-T" option to enable it on Unix/Linux.
Reference:
KB-1698: Troubleshooting Single Sign On (SSO) issues
KB-1876: Cannot create Kerberos tickets using Centrify OpenSSH
KB-5452: How to enable debug for PuTTy / SSH clients?KB-3285: How to Collect Debug Logs from an OpenSSH Server





